ASA Lessons: Static PAT
I decided a while back I would spend a bit of time learning about the Cisco ASA firewall. This is the first post surrounding some technologies I have explored during that time.
For some of you it might be easy stuff, but for others, including myself, might find it interesting for reference.
One of the most used functions of a firewall is to provide NAT functions. The first one of the different modes of NAT i want to illustrate is Static PAT (Port Address Translation).
So what is it? – Well, basically its a way to make a static mapping from one port to another (or the same as you will see).
Let me elaborate on that after you take a look at the topology.
This is the topology we will be using for this demonstration:
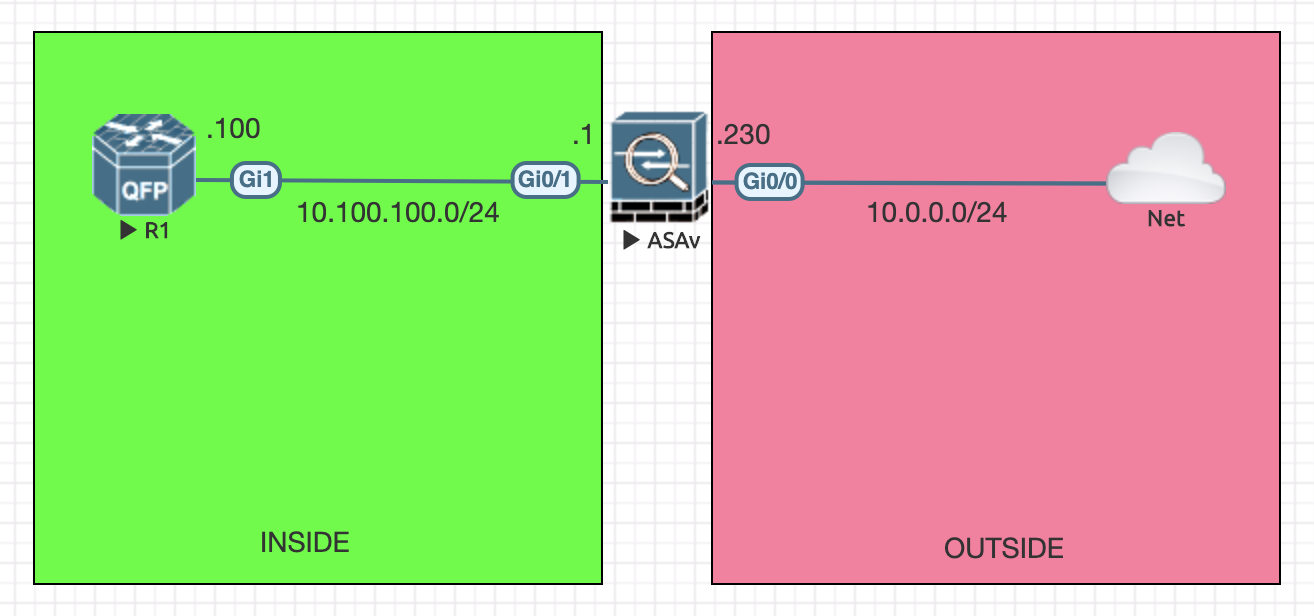
In this very straight forward topology we have an ASA fronting a CSR router which will act as our “inside” host. The ASA is also connected to an “outside” network, which is my home lab network.
Our static PAT configuration will accomplish the following:
- Connections to tcp port 23 (Telnet) to the ASA’s outside interface address (10.0.0.230) will be translated to R1’s G1 interface address (10.100.100.100).
- Connections to tcp port 80 (HTTP) to the ASA’s outside interface address (10.0.0.230) will be translated to R1’s G1 interface address (10.100.100.100).
- Connections to tcp port 443 (HTTPS) to the ASA’s outside interface address (10.0.0.230) will be translated to R1’s G1 interface address (10.100.100.100).
One way to accomplish this is to use Object based NAT, which is not what I will show here. I will be using the “traditional” way of doing static PAT.
However, before we go into this configuration, lets verify our interface configuration on the ASA:
interface GigabitEthernet0/0
nameif out
security-level 0
ip address 10.0.0.230 255.255.255.0
!
interface GigabitEthernet0/1
nameif IN
security-level 100
ip address 10.100.100.1 255.255.255.0 So lets go ahead and define some objects we will be using for this example:
object service HTTPS_SERVICE
service tcp source eq https
object service HTTP_SERVICE
service tcp source eq www
object service TELNET_SERVICE
service tcp source eq telnet
object network R1-LAN-INTERFACE
host 10.100.100.100As can be seen, we have defined 3 service objects (HTTPS_SERVICE, HTTP_SERVICE and TELNET_SERVICE) representing the different ports we want PAT’ed towards R1.
Beyond that, we have defined R1’s lan interface using a network object.
Since we are using traditional based Static PAT, we will then define our NAT statements:
nat (IN,out) source static R1-LAN-INTERFACE interface service HTTP_SERVICE HTTP_SERVICE
nat (IN,out) source static R1-LAN-INTERFACE interface service HTTPS_SERVICE HTTPS_SERVICE
nat (IN,out) source static R1-LAN-INTERFACE interface service TELNET_SERVICE TELNET_SERVICELets do some verification before we proceed:
ASAv1# sh nat
Manual NAT Policies (Section 1)
1 (IN) to (out) source static R1-LAN-INTERFACE interface service HTTP_SERVICE HTTP_SERVICE
translate_hits = 185, untranslate_hits = 202
2 (IN) to (out) source static R1-LAN-INTERFACE interface service HTTPS_SERVICE HTTPS_SERVICE
translate_hits = 20, untranslate_hits = 20
3 (IN) to (out) source static R1-LAN-INTERFACE interface service TELNET_SERVICE TELNET_SERVICE
translate_hits = 2, untranslate_hits = 5
ASAv1# sh xlate
6 in use, 6 most used
Flags: D - DNS, e - extended, I - identity, i - dynamic, r - portmap,
s - static, T - twice, N - net-to-net
TCP PAT from IN:10.100.100.100 80-80 to out:10.0.0.230 80-80
flags srT idle 1:41:50 timeout 0:00:00
TCP PAT from out:0.0.0.0/0 0 to IN:0.0.0.0/0 0
flags srIT idle 1:41:50 timeout 0:00:00
TCP PAT from IN:10.100.100.100 443-443 to out:10.0.0.230 443-443
flags srT idle 1:52:46 timeout 0:00:00
TCP PAT from out:0.0.0.0/0 0 to IN:0.0.0.0/0 0
flags srIT idle 1:52:46 timeout 0:00:00
TCP PAT from IN:10.100.100.100 23-23 to out:10.0.0.230 23-23
flags srT idle 1:55:10 timeout 0:00:00
TCP PAT from out:0.0.0.0/0 0 to IN:0.0.0.0/0 0
flags srIT idle 1:55:10 timeout 0:00:00From the output we can see that we have 3 “Manual NAT Policies”. We can see that NAT rule nr. 1 is when we go from the “IN” zone going to the “out” zone.
We will be targeting/sourcing from R1-LAN-INTERFACE object which points to R1’s G1 interface and we will translate/NAT it to the outside interface address.
The PAT part is where our service is defined. We will only do this NAT when its HTTP, HTTPS and Telnet, equal to port 80, 443 and 23.
If you take this configuration and apply it in your own lab, it will not work… yet. What we need to take care of is an access-list.
The reason behind this is that our “outside” interface is in security-level 0 and “inside” is in 100, which means we need to apply an access-list inbound on the “out” interface:
ASAv1# sh run access-list
access-list OUTSIDE_TO_INSIDE extended permit tcp any object R1-LAN-INTERFACE eq https
access-list OUTSIDE_TO_INSIDE extended permit tcp any object R1-LAN-INTERFACE eq www
access-list OUTSIDE_TO_INSIDE extended permit tcp any object R1-LAN-INTERFACE eq telnet
ASAv1# sh run access-group
access-group OUTSIDE_TO_INSIDE in interface outHaving applied the access-list, you should be ready to test out your new Static NAT configuration (done from a host within my home-lab sitting on the “outside” network):
kp@shell-server:~$ telnet 10.0.0.230
Trying 10.0.0.230...
Connected to 10.0.0.230.
Escape character is '^]'.
User Access Verification
Password:
R1#
kp@shell-server:~$ telnet 10.0.0.230 80
Trying 10.0.0.230...
Connected to 10.0.0.230.
Escape character is '^]'.
get /
<html>
<head><title>400 Bad Request</title></head>
<body bgcolor="white">
<center><h1>400 Bad Request</h1></center>
<hr><center>nginx</center>
</body>
</html>
Connection closed by foreign host.And thats basically it. From going through this example, you should have the knowledge to perform very simply Static PAT on your ASA.
Until next time!
/Kim